mirror of
https://github.com/snail007/goproxy
synced 2024-11-06 09:20:28 +00:00
update
This commit is contained in:
parent
93a052dd3d
commit
a156abe49e
@ -248,7 +248,7 @@ The format is: `-p 0.0.0.0:80,0.0.0.0:443,.0.0.0.0:8000-9000,:5000-6000`, more T
|
|||||||
|
|
||||||
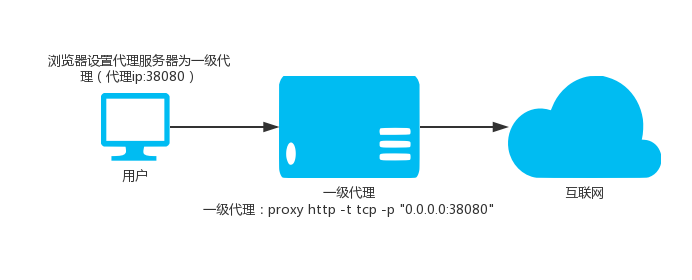
### 1.1. Ordinary level HTTP proxy
|
### 1.1. Ordinary level HTTP proxy
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
`proxy http -t tcp -p "0.0.0.0:38080"`
|
`proxy http -t tcp -p "0.0.0.0:38080"`
|
||||||
|
|
||||||
@ -262,7 +262,7 @@ Listen port argument `-p` can be:
|
|||||||
|
|
||||||
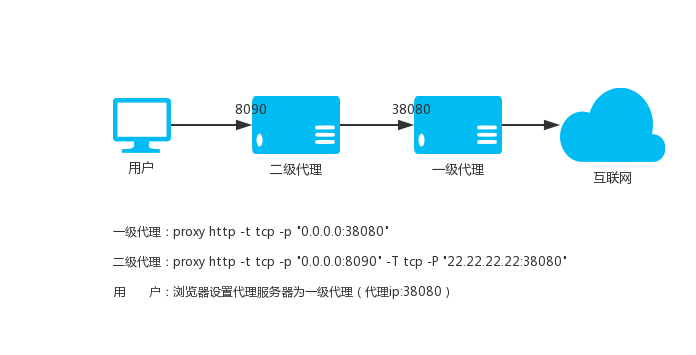
### 1.2. Ordinary secondary HTTP proxy
|
### 1.2. Ordinary secondary HTTP proxy
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
Use local port 8090, assuming the upstream HTTP proxy is `22.22.22.22:8080`
|
Use local port 8090, assuming the upstream HTTP proxy is `22.22.22.22:8080`
|
||||||
|
|
||||||
@ -276,7 +276,7 @@ We can also specify the black and white list file of the website domain name, on
|
|||||||
|
|
||||||
> Note: The `proxy.crt` and `proxy.key` used by the secondary proxy should be consistent with the primary proxy.
|
> Note: The `proxy.crt` and `proxy.key` used by the secondary proxy should be consistent with the primary proxy.
|
||||||
|
|
||||||

|
|
||||||
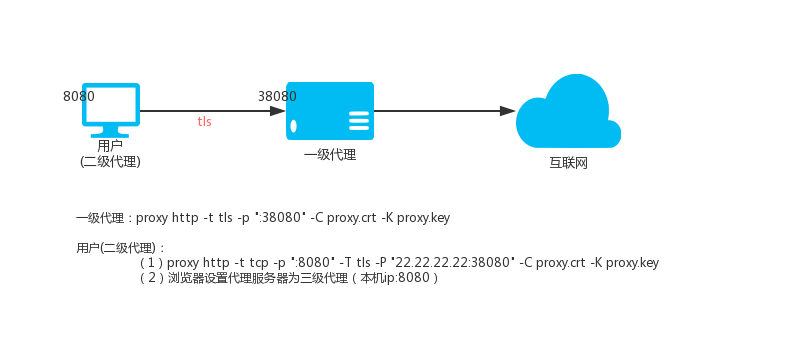
Level 1 HTTP proxy (VPS, IP: 22.22.22.22)
|
Level 1 HTTP proxy (VPS, IP: 22.22.22.22)
|
||||||
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
@ -289,7 +289,7 @@ Secondary HTTP proxy (local windows)
|
|||||||
Then set your windos system, the proxy that needs to go through the proxy Internet program is http mode, the address is: 127.0.0.1, the port is: 8080, the program can access the Internet through vps through the encrypted channel.
|
Then set your windos system, the proxy that needs to go through the proxy Internet program is http mode, the address is: 127.0.0.1, the port is: 8080, the program can access the Internet through vps through the encrypted channel.
|
||||||
|
|
||||||
### 1.4.HTTP Level 3 Agent (Encryption)
|
### 1.4.HTTP Level 3 Agent (Encryption)
|
||||||

|

|
||||||
Level 1 HTTP proxy VPS_01, IP: 22.22.22.22
|
Level 1 HTTP proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
Secondary HTTP proxy VPS_02, IP: 33.33.33.33
|
Secondary HTTP proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -326,7 +326,7 @@ By default, the proxy will intelligently determine whether a website domain name
|
|||||||
`proxy http --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
`proxy http --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
### 1.7.HTTP(S) via SSH relay
|
### 1.7.HTTP(S) via SSH relay
|
||||||

|
|
||||||
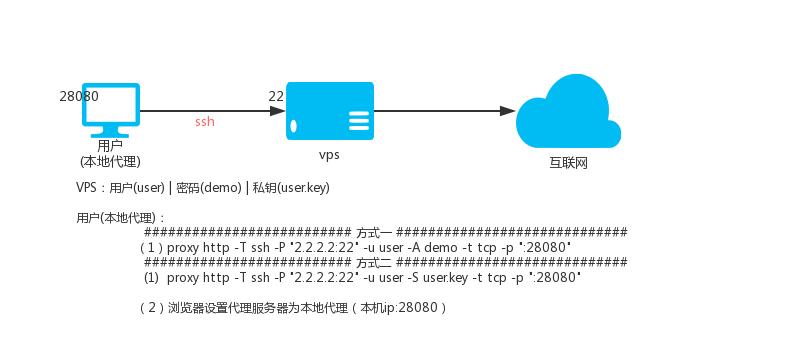
Description: The principle of ssh transfer is to use the forwarding function of ssh, that is, after you connect to ssh, you can access the target address through ssh proxy.
|
Description: The principle of ssh transfer is to use the forwarding function of ssh, that is, after you connect to ssh, you can access the target address through ssh proxy.
|
||||||
Suppose there is: vps
|
Suppose there is: vps
|
||||||
- IP is 2.2.2.2, ssh port is 22, ssh username is: user, ssh user password is: demo
|
- IP is 2.2.2.2, ssh port is 22, ssh username is: user, ssh user password is: demo
|
||||||
@ -340,7 +340,7 @@ Local HTTP(S) proxy port 28080, executing:
|
|||||||
`proxy http -T ssh -P "2.2.2.2:22" -u user -S user.key -t tcp -p ":28080"`
|
`proxy http -T ssh -P "2.2.2.2:22" -u user -S user.key -t tcp -p ":28080"`
|
||||||
|
|
||||||
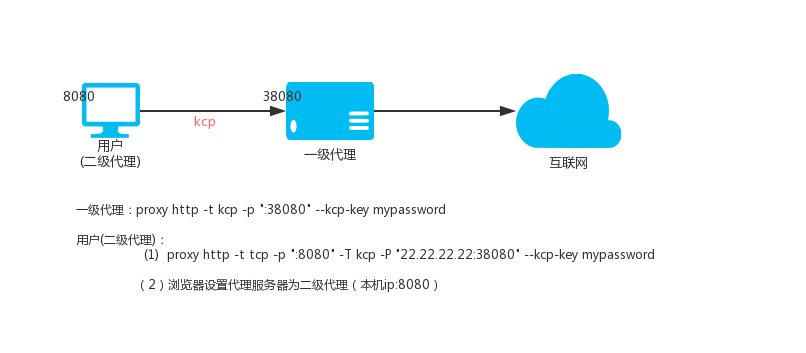
### 1.8.KCP protocol transmission
|
### 1.8.KCP protocol transmission
|
||||||

|
|
||||||
The KCP protocol requires the --kcp-key parameter to set a password for encrypting and decrypting data.
|
The KCP protocol requires the --kcp-key parameter to set a password for encrypting and decrypting data.
|
||||||
|
|
||||||
Level 1 HTTP proxy (VPS, IP: 22.22.22.22)
|
Level 1 HTTP proxy (VPS, IP: 22.22.22.22)
|
||||||
@ -351,7 +351,7 @@ Secondary HTTP proxy (local Linux)
|
|||||||
Then access the local port 8080 is to access the proxy port 38080 on the VPS, the data is transmitted through the kcp protocol, note that the kcp is the udp protocol, so the firewall needs to release the 380p udp protocol.
|
Then access the local port 8080 is to access the proxy port 38080 on the VPS, the data is transmitted through the kcp protocol, note that the kcp is the udp protocol, so the firewall needs to release the 380p udp protocol.
|
||||||
|
|
||||||
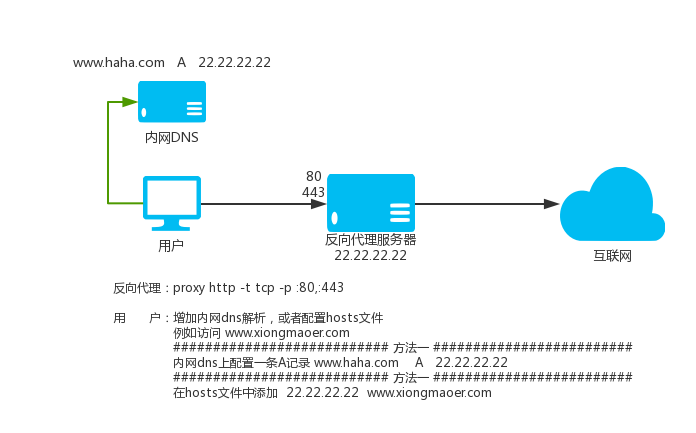
### 1.9 HTTP(S) Reverse Proxy
|
### 1.9 HTTP(S) Reverse Proxy
|
||||||

|
|
||||||
The proxy not only supports the proxy setting in other software, but also provides proxy services for other software. It also supports directly parsing the requested website domain name to the proxy listening ip, and then the proxy listens to the 80 and 443 ports, then the proxy will automatically You proxy access to the HTTP(S) website you need to access.
|
The proxy not only supports the proxy setting in other software, but also provides proxy services for other software. It also supports directly parsing the requested website domain name to the proxy listening ip, and then the proxy listens to the 80 and 443 ports, then the proxy will automatically You proxy access to the HTTP(S) website you need to access.
|
||||||
|
|
||||||
How to use:
|
How to use:
|
||||||
@ -517,7 +517,7 @@ The meaning of each value is as follows:
|
|||||||
## 2.TCP Proxies
|
## 2.TCP Proxies
|
||||||
|
|
||||||
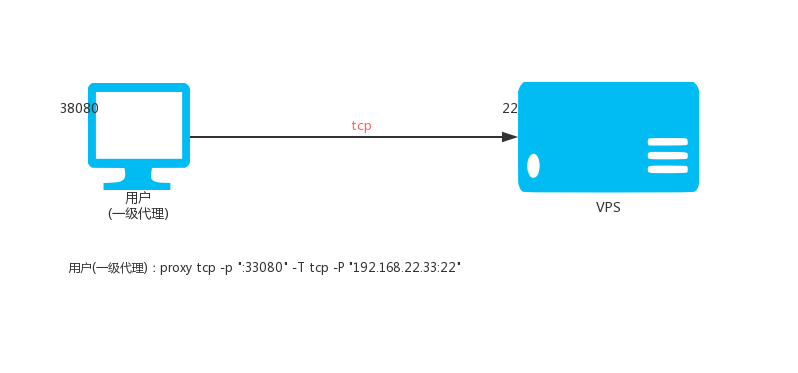
### 2.1. Ordinary level TCP proxy
|
### 2.1. Ordinary level TCP proxy
|
||||||

|
|
||||||
Local execution:
|
Local execution:
|
||||||
`proxy tcp -p ":33080" -T tcp -P "192.168.22.33:22"`
|
`proxy tcp -p ":33080" -T tcp -P "192.168.22.33:22"`
|
||||||
Then access the local port 33080 is to access port 22 of 192.168.22.33.
|
Then access the local port 33080 is to access port 22 of 192.168.22.33.
|
||||||
@ -545,7 +545,7 @@ If you want to connect the ports of `33080`, `33081`, etc. to the `22` port of 1
|
|||||||
`proxy tcp -p ":33080-33085" -T tcp -P "192.168.22.33:22" --lock-port`
|
`proxy tcp -p ":33080-33085" -T tcp -P "192.168.22.33:22" --lock-port`
|
||||||
|
|
||||||
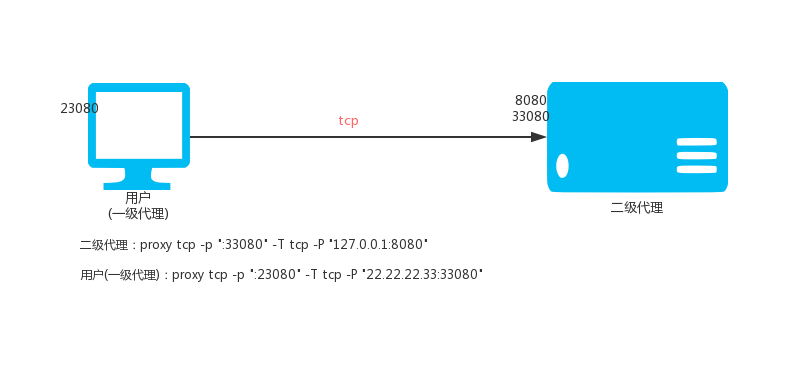
### 2.2. Ordinary secondary TCP proxy
|
### 2.2. Ordinary secondary TCP proxy
|
||||||

|
|
||||||
VPS (IP: 22.22.2.33) is executed:
|
VPS (IP: 22.22.2.33) is executed:
|
||||||
`proxy tcp -p ":33080" -T tcp -P "127.0.0.1:8080"`
|
`proxy tcp -p ":33080" -T tcp -P "127.0.0.1:8080"`
|
||||||
Local execution:
|
Local execution:
|
||||||
@ -553,7 +553,7 @@ Local execution:
|
|||||||
Then access the local port 23080 is to access port 8020 of 22.22.22.33.
|
Then access the local port 23080 is to access port 8020 of 22.22.22.33.
|
||||||
|
|
||||||
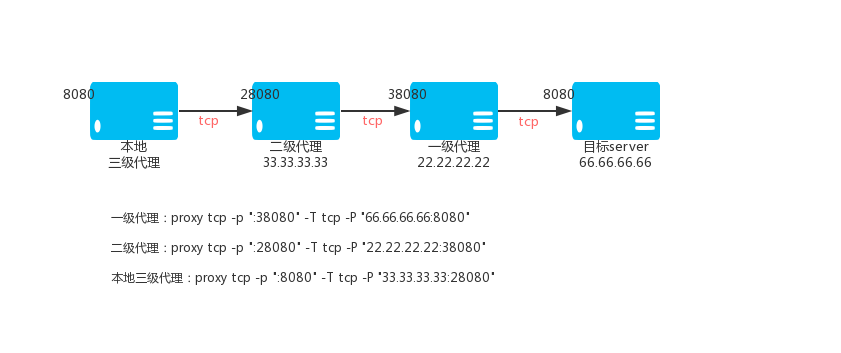
### 2.3. Ordinary three-level TCP proxy
|
### 2.3. Ordinary three-level TCP proxy
|
||||||

|
|
||||||
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy tcp -p ":38080" -T tcp -P "66.66.66.66:8080"`
|
`proxy tcp -p ":38080" -T tcp -P "66.66.66.66:8080"`
|
||||||
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -563,7 +563,7 @@ Level 3 TCP proxy (local)
|
|||||||
Then access the local port 8080 is to access the port 8080 of 66.66.66.66 through the encrypted TCP tunnel.
|
Then access the local port 8080 is to access the port 8080 of 66.66.66.66 through the encrypted TCP tunnel.
|
||||||
|
|
||||||
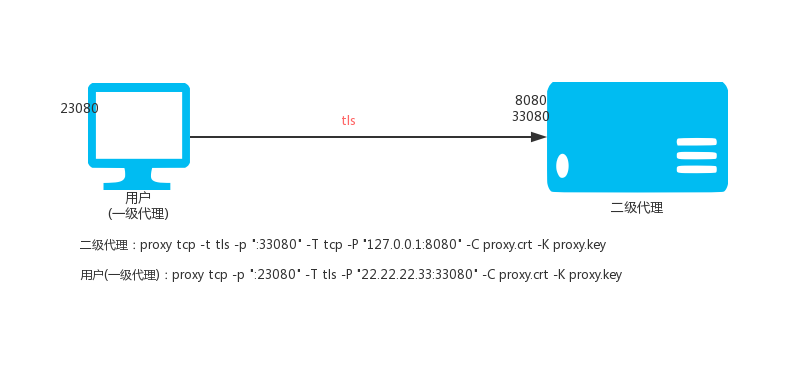
### 2.4. Encrypting secondary TCP proxy
|
### 2.4. Encrypting secondary TCP proxy
|
||||||

|
|
||||||
VPS (IP: 22.22.2.33) is executed:
|
VPS (IP: 22.22.2.33) is executed:
|
||||||
`proxy tcp -t tls -p ":33080" -T tcp -P "127.0.0.1:8080" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":33080" -T tcp -P "127.0.0.1:8080" -C proxy.crt -K proxy.key`
|
||||||
Local execution:
|
Local execution:
|
||||||
@ -571,7 +571,7 @@ Local execution:
|
|||||||
Then access the local port 23080 is to access the port 8080 of 22.22.22.33 through the encrypted TCP tunnel.
|
Then access the local port 23080 is to access the port 8080 of 22.22.22.33 through the encrypted TCP tunnel.
|
||||||
|
|
||||||
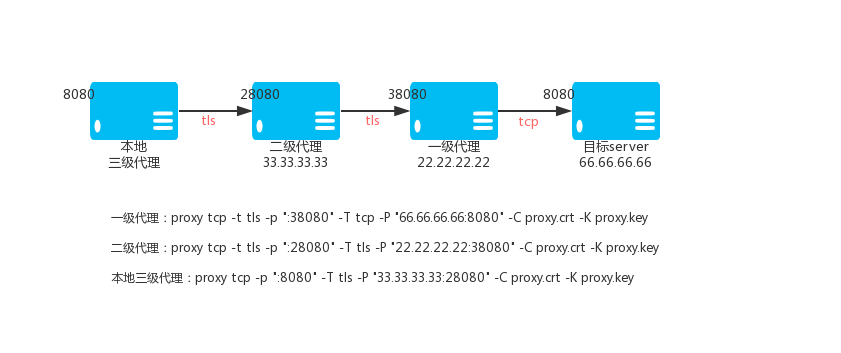
### 2.5.Encrypting Level 3 TCP Agent
|
### 2.5.Encrypting Level 3 TCP Agent
|
||||||

|
|
||||||
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy tcp -t tls -p ":38080" -T tcp -P "66.66.66.66:8080" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":38080" -T tcp -P "66.66.66.66:8080" -C proxy.crt -K proxy.key`
|
||||||
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -631,7 +631,7 @@ Local execution:
|
|||||||
## 3.UDP Proxies
|
## 3.UDP Proxies
|
||||||
|
|
||||||
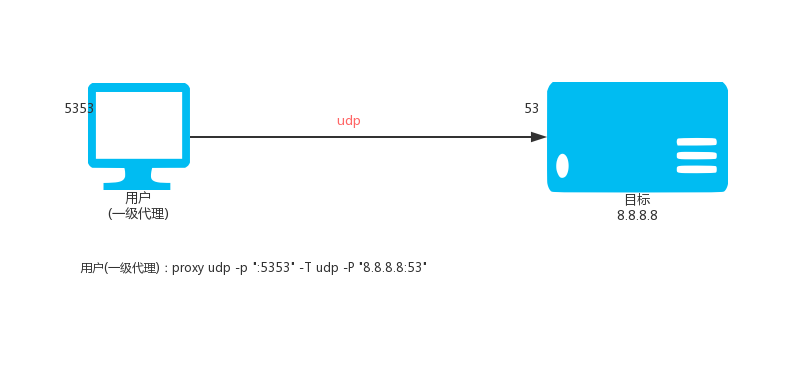
### 3.1. Ordinary UDP proxy
|
### 3.1. Ordinary UDP proxy
|
||||||

|
|
||||||
Local execution:
|
Local execution:
|
||||||
`proxy udp -p ":5353" -T udp -P "8.8.8.8:53"`
|
`proxy udp -p ":5353" -T udp -P "8.8.8.8:53"`
|
||||||
Then access the local UDP: 5353 port is to access 8.8.8.8 UDP: 53 port.
|
Then access the local UDP: 5353 port is to access 8.8.8.8 UDP: 53 port.
|
||||||
@ -659,7 +659,7 @@ If you want to connect the ports of `33080`, `33081`, etc. to the `2222` port of
|
|||||||
`proxy udp -p ":33080-33085" -T udp -P "192.168.22.33:2222" --lock-port`
|
`proxy udp -p ":33080-33085" -T udp -P "192.168.22.33:2222" --lock-port`
|
||||||
|
|
||||||
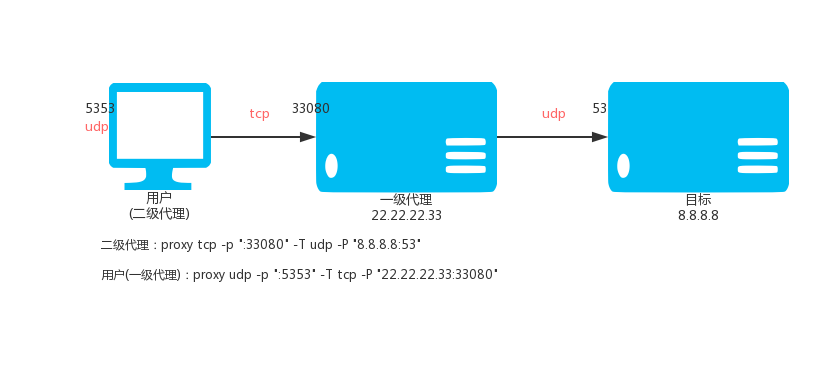
### 3.2. Ordinary secondary UDP proxy
|
### 3.2. Ordinary secondary UDP proxy
|
||||||

|
|
||||||
VPS (IP: 22.22.2.33) is executed:
|
VPS (IP: 22.22.2.33) is executed:
|
||||||
`proxy tcp -p ":33080" -T udp -P "8.8.8.8:53"`
|
`proxy tcp -p ":33080" -T udp -P "8.8.8.8:53"`
|
||||||
Local execution:
|
Local execution:
|
||||||
@ -667,7 +667,7 @@ Local execution:
|
|||||||
Then access the local UDP: 5353 port is through the TCP tunnel, through the VPS access 8.8.8.8 UDP: 53 port.
|
Then access the local UDP: 5353 port is through the TCP tunnel, through the VPS access 8.8.8.8 UDP: 53 port.
|
||||||
|
|
||||||
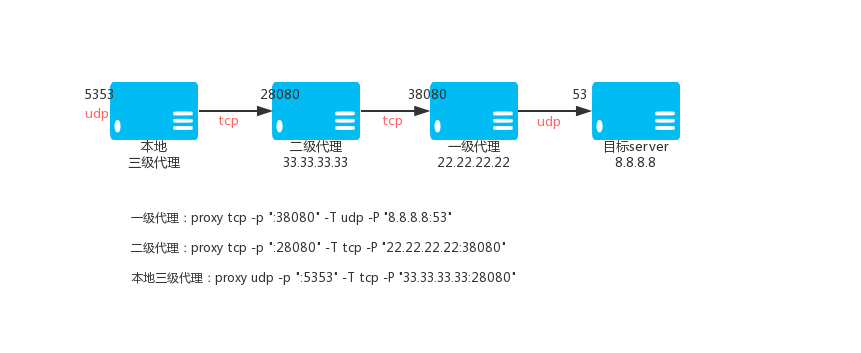
### 3.3. Ordinary three-level UDP proxy
|
### 3.3. Ordinary three-level UDP proxy
|
||||||

|
|
||||||
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy tcp -p ":38080" -T udp -P "8.8.8.8:53"`
|
`proxy tcp -p ":38080" -T udp -P "8.8.8.8:53"`
|
||||||
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -677,7 +677,7 @@ Level 3 TCP proxy (local)
|
|||||||
Then access to the local 5353 port is through the TCP tunnel, through the VPS to access port 8.8.8.8.
|
Then access to the local 5353 port is through the TCP tunnel, through the VPS to access port 8.8.8.8.
|
||||||
|
|
||||||
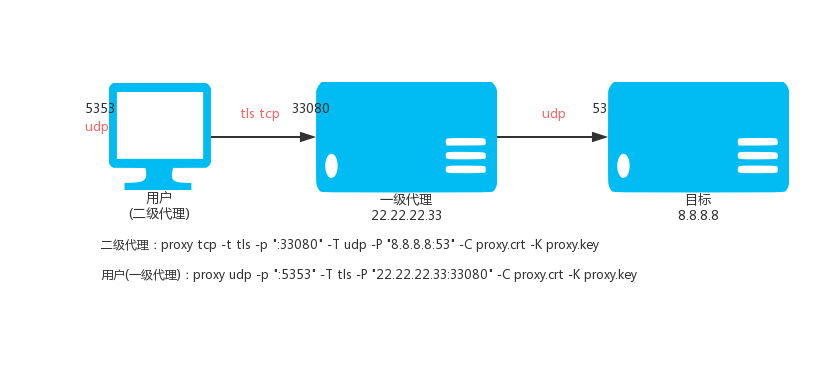
### 3.4. Encrypting secondary UDP proxy
|
### 3.4. Encrypting secondary UDP proxy
|
||||||

|
|
||||||
VPS (IP: 22.22.2.33) is executed:
|
VPS (IP: 22.22.2.33) is executed:
|
||||||
`proxy tcp -t tls -p ":33080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":33080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
||||||
Local execution:
|
Local execution:
|
||||||
@ -685,7 +685,7 @@ Local execution:
|
|||||||
Then access the local UDP: 5353 port is through the encrypted TCP tunnel, through the VPS access 8.8.8.8 UDP: 53 port.
|
Then access the local UDP: 5353 port is through the encrypted TCP tunnel, through the VPS access 8.8.8.8 UDP: 53 port.
|
||||||
|
|
||||||
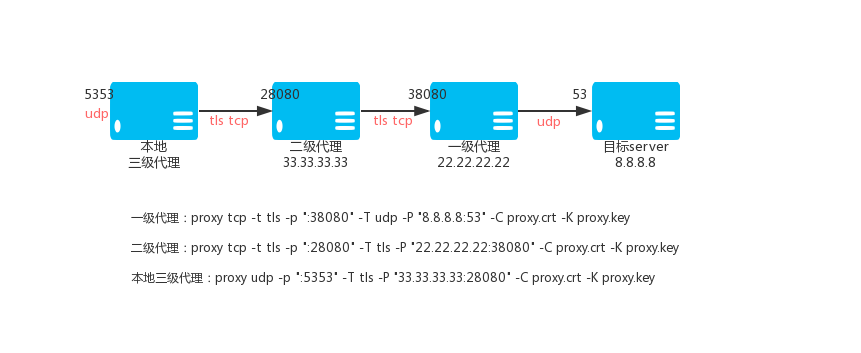
### 3.5. Encryption Level 3 UDP Agent
|
### 3.5. Encryption Level 3 UDP Agent
|
||||||

|
|
||||||
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
Primary TCP proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy tcp -t tls -p ":38080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":38080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
||||||
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
Secondary TCP proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -932,14 +932,14 @@ Listen port argument `-p` can be:
|
|||||||
```
|
```
|
||||||
|
|
||||||
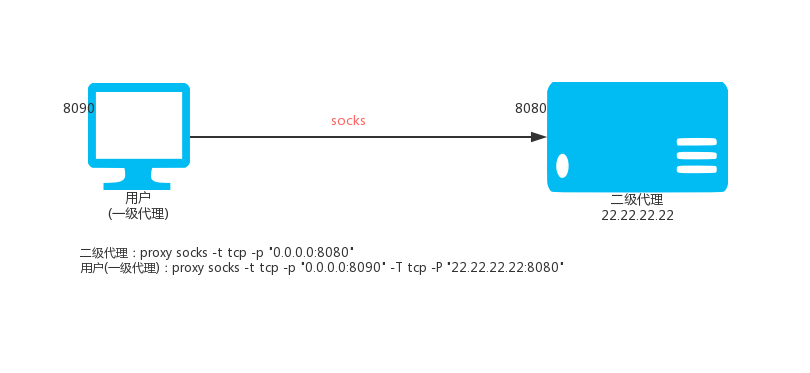
### 5.2. Ordinary secondary SOCKS5 agent
|
### 5.2. Ordinary secondary SOCKS5 agent
|
||||||

|
|
||||||
Use local port 8090, assuming the upstream SOCKS5 proxy is `22.22.22.22:8080`
|
Use local port 8090, assuming the upstream SOCKS5 proxy is `22.22.22.22:8080`
|
||||||
`proxy socks -t tcp -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" `
|
`proxy socks -t tcp -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" `
|
||||||
We can also specify the black and white list file of the website domain name, one domain name and one domain name, the matching rule is the rightmost match, for example: baidu.com, the match is *.*.baidu.com, the blacklist domain name domain name goes directly to the upstream agent, white The domain name of the list does not go to the upstream agent; if the domain name is in the blacklist and in the whitelist, the blacklist works.
|
We can also specify the black and white list file of the website domain name, one domain name and one domain name, the matching rule is the rightmost match, for example: baidu.com, the match is *.*.baidu.com, the blacklist domain name domain name goes directly to the upstream agent, white The domain name of the list does not go to the upstream agent; if the domain name is in the blacklist and in the whitelist, the blacklist works.
|
||||||
`proxy socks -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" -b blocked.txt -d direct.txt`
|
`proxy socks -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" -b blocked.txt -d direct.txt`
|
||||||
|
|
||||||
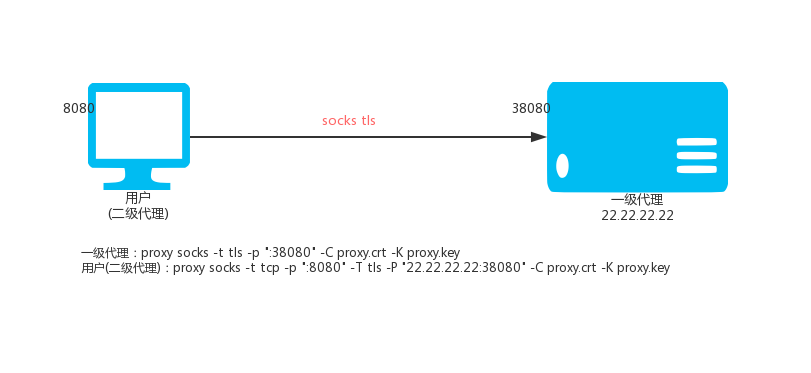
### 5.3. SOCKS Level 2 Agent (Encryption)
|
### 5.3. SOCKS Level 2 Agent (Encryption)
|
||||||

|
|
||||||
Level 1 SOCKS proxy (VPS, IP: 22.22.22.22)
|
Level 1 SOCKS proxy (VPS, IP: 22.22.22.22)
|
||||||
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
@ -952,7 +952,7 @@ Secondary SOCKS proxy (local windows)
|
|||||||
Then set your windos system, the proxy that needs to go through the proxy Internet program is the socks5 mode, the address is: 127.0.0.1, the port is: 8080, the program can access the Internet through vps through the encrypted channel.
|
Then set your windos system, the proxy that needs to go through the proxy Internet program is the socks5 mode, the address is: 127.0.0.1, the port is: 8080, the program can access the Internet through vps through the encrypted channel.
|
||||||
|
|
||||||
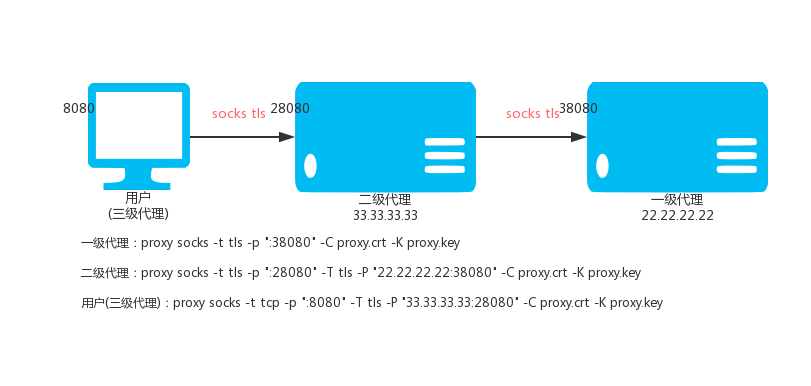
### 5.4. SOCKS Level 3 Agent (Encryption)
|
### 5.4. SOCKS Level 3 Agent (Encryption)
|
||||||

|
|
||||||
Level 1 SOCKS proxy VPS_01, IP: 22.22.22.22
|
Level 1 SOCKS proxy VPS_01, IP: 22.22.22.22
|
||||||
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
Secondary SOCKS proxy VPS_02, IP: 33.33.33.33
|
Secondary SOCKS proxy VPS_02, IP: 33.33.33.33
|
||||||
@ -966,7 +966,7 @@ By default, the proxy will intelligently determine whether a website domain name
|
|||||||
`proxy socks --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
`proxy socks --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
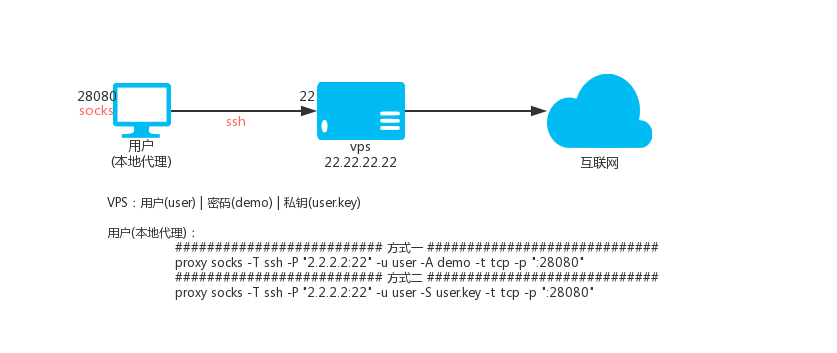
### 5.6. SOCKS via SSH relay
|
### 5.6. SOCKS via SSH relay
|
||||||

|
|
||||||
Description: The principle of ssh transfer is to use the forwarding function of ssh, that is, after you connect to ssh, you can access the target address through ssh proxy.
|
Description: The principle of ssh transfer is to use the forwarding function of ssh, that is, after you connect to ssh, you can access the target address through ssh proxy.
|
||||||
Suppose there is: vps
|
Suppose there is: vps
|
||||||
- IP is 2.2.2.2, ssh port is 22, ssh username is: user, ssh user password is: demo
|
- IP is 2.2.2.2, ssh port is 22, ssh username is: user, ssh user password is: demo
|
||||||
@ -1201,7 +1201,7 @@ The command is as follows:
|
|||||||
`proxy sps -S ss -H aes-256-cfb -J pass -T tcp -P 127.0.0.1:8080 -t tcp -p :18080 -h aes-192-cfb -j pass`.
|
`proxy sps -S ss -H aes-256-cfb -J pass -T tcp -P 127.0.0.1:8080 -t tcp -p :18080 -h aes-192-cfb -j pass`.
|
||||||
|
|
||||||
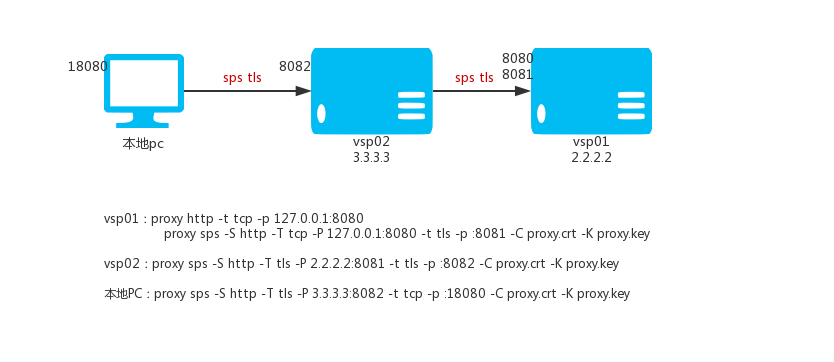
### 6.5 Chained connection
|
### 6.5 Chained connection
|
||||||

|
|
||||||
The above mentioned multiple sps nodes can be connected to build encrypted channels in a hierarchical connection, assuming the following vps and the home PC.
|
The above mentioned multiple sps nodes can be connected to build encrypted channels in a hierarchical connection, assuming the following vps and the home PC.
|
||||||
Vps01:2.2.2.2
|
Vps01:2.2.2.2
|
||||||
Vps02:3.3.3.3
|
Vps02:3.3.3.3
|
||||||
@ -1734,7 +1734,7 @@ The `--traffic-url` URL must response the HTTP status code` 204`. Only when the
|
|||||||
|
|
||||||
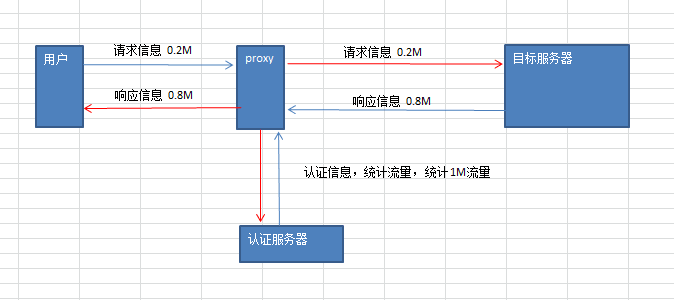
#### traffic flow
|
#### traffic flow
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
|
|
||||||
### Disconnect the user's connection
|
### Disconnect the user's connection
|
||||||
|
|||||||
@ -274,7 +274,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
|
|
||||||
### 1.1.普通一级HTTP代理
|
### 1.1.普通一级HTTP代理
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
`proxy http -t tcp -p "0.0.0.0:38080"`
|
`proxy http -t tcp -p "0.0.0.0:38080"`
|
||||||
|
|
||||||
@ -288,7 +288,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
|
|
||||||
### 1.2.普通二级HTTP代理
|
### 1.2.普通二级HTTP代理
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
使用本地端口8090,假设上级HTTP代理是`22.22.22.22:8080`
|
使用本地端口8090,假设上级HTTP代理是`22.22.22.22:8080`
|
||||||
|
|
||||||
@ -302,7 +302,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
|
|
||||||
> 注意: 后面二级代理使用的`proxy.crt`和`proxy.key`应与一级代理一致
|
> 注意: 后面二级代理使用的`proxy.crt`和`proxy.key`应与一级代理一致
|
||||||
|
|
||||||

|

|
||||||
一级HTTP代理(VPS,IP:22.22.22.22)
|
一级HTTP代理(VPS,IP:22.22.22.22)
|
||||||
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
@ -315,7 +315,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
然后设置你的windos系统中,需要通过代理上网的程序的代理为http模式,地址为:127.0.0.1,端口为:8080,程序即可通过加密通道通过vps上网。
|
然后设置你的windos系统中,需要通过代理上网的程序的代理为http模式,地址为:127.0.0.1,端口为:8080,程序即可通过加密通道通过vps上网。
|
||||||
|
|
||||||
### 1.4.HTTP三级代理(加密)
|
### 1.4.HTTP三级代理(加密)
|
||||||

|

|
||||||
一级HTTP代理VPS_01,IP:22.22.22.22
|
一级HTTP代理VPS_01,IP:22.22.22.22
|
||||||
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
`proxy http -t tls -p ":38080" -C proxy.crt -K proxy.key`
|
||||||
二级HTTP代理VPS_02,IP:33.33.33.33
|
二级HTTP代理VPS_02,IP:33.33.33.33
|
||||||
@ -333,7 +333,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
`proxy http --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
`proxy http --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key`
|
||||||
|
|
||||||
### 1.7.HTTP(S)通过SSH中转
|
### 1.7.HTTP(S)通过SSH中转
|
||||||

|

|
||||||
说明:ssh中转的原理是利用了ssh的转发功能,就是你连接上ssh之后,可以通过ssh代理访问目标地址。
|
说明:ssh中转的原理是利用了ssh的转发功能,就是你连接上ssh之后,可以通过ssh代理访问目标地址。
|
||||||
假设有:vps
|
假设有:vps
|
||||||
- IP是2.2.2.2, ssh端口是22, ssh用户名是:user, ssh用户密码是:demo
|
- IP是2.2.2.2, ssh端口是22, ssh用户名是:user, ssh用户密码是:demo
|
||||||
@ -347,7 +347,7 @@ socks5\sps\http代理,控制客户端并发连接数参数是:`--max-conns-rate`
|
|||||||
`proxy http -T ssh -P "2.2.2.2:22" -u user -S user.key -t tcp -p ":28080"`
|
`proxy http -T ssh -P "2.2.2.2:22" -u user -S user.key -t tcp -p ":28080"`
|
||||||
|
|
||||||
### 1.8.KCP协议传输
|
### 1.8.KCP协议传输
|
||||||

|

|
||||||
KCP协议需要--kcp-key参数设置一个密码用于加密解密数据
|
KCP协议需要--kcp-key参数设置一个密码用于加密解密数据
|
||||||
|
|
||||||
一级HTTP代理(VPS,IP:22.22.22.22)
|
一级HTTP代理(VPS,IP:22.22.22.22)
|
||||||
@ -358,7 +358,7 @@ KCP协议需要--kcp-key参数设置一个密码用于加密解密数据
|
|||||||
那么访问本地的8080端口就是访问VPS上面的代理端口38080,数据通过kcp协议传输,注意kcp走的是udp协议协议,所以防火墙需放开38080的udp协议。
|
那么访问本地的8080端口就是访问VPS上面的代理端口38080,数据通过kcp协议传输,注意kcp走的是udp协议协议,所以防火墙需放开38080的udp协议。
|
||||||
|
|
||||||
### 1.9 HTTP(S)反向代理
|
### 1.9 HTTP(S)反向代理
|
||||||

|

|
||||||
proxy不仅支持在其他软件里面通过设置代理的方式,为其他软件提供代理服务,而且支持直接把请求的网站域名解析到proxy监听的ip上,然后proxy监听80和443端口,那么proxy就会自动为你代理访问需要访问的HTTP(S)网站。
|
proxy不仅支持在其他软件里面通过设置代理的方式,为其他软件提供代理服务,而且支持直接把请求的网站域名解析到proxy监听的ip上,然后proxy监听80和443端口,那么proxy就会自动为你代理访问需要访问的HTTP(S)网站。
|
||||||
|
|
||||||
使用方式:
|
使用方式:
|
||||||
@ -549,7 +549,7 @@ HTTP(S)代理支持上级负载均衡,多个上级重复-P参数即可。
|
|||||||
## 2.TCP代理
|
## 2.TCP代理
|
||||||
|
|
||||||
### 2.1 普通一级TCP代理
|
### 2.1 普通一级TCP代理
|
||||||

|

|
||||||
本地执行:
|
本地执行:
|
||||||
`proxy tcp -p ":33080" -T tcp -P "192.168.22.33:22"`
|
`proxy tcp -p ":33080" -T tcp -P "192.168.22.33:22"`
|
||||||
那么访问本地33080端口就是访问192.168.22.33的22端口。
|
那么访问本地33080端口就是访问192.168.22.33的22端口。
|
||||||
@ -578,7 +578,7 @@ HTTP(S)代理支持上级负载均衡,多个上级重复-P参数即可。
|
|||||||
|
|
||||||
|
|
||||||
### 2.2 普通二级TCP代理
|
### 2.2 普通二级TCP代理
|
||||||

|

|
||||||
VPS(IP:22.22.22.33)执行:
|
VPS(IP:22.22.22.33)执行:
|
||||||
`proxy tcp -p ":33080" -T tcp -P "127.0.0.1:8080"`
|
`proxy tcp -p ":33080" -T tcp -P "127.0.0.1:8080"`
|
||||||
本地执行:
|
本地执行:
|
||||||
@ -586,7 +586,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地23080端口就是访问22.22.22.33的8080端口。
|
那么访问本地23080端口就是访问22.22.22.33的8080端口。
|
||||||
|
|
||||||
### 2.3 普通三级TCP代理
|
### 2.3 普通三级TCP代理
|
||||||

|

|
||||||
一级TCP代理VPS_01,IP:22.22.22.22
|
一级TCP代理VPS_01,IP:22.22.22.22
|
||||||
`proxy tcp -p ":38080" -T tcp -P "66.66.66.66:8080"`
|
`proxy tcp -p ":38080" -T tcp -P "66.66.66.66:8080"`
|
||||||
二级TCP代理VPS_02,IP:33.33.33.33
|
二级TCP代理VPS_02,IP:33.33.33.33
|
||||||
@ -596,7 +596,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地8080端口就是通过加密TCP隧道访问66.66.66.66的8080端口。
|
那么访问本地8080端口就是通过加密TCP隧道访问66.66.66.66的8080端口。
|
||||||
|
|
||||||
### 2.4 加密二级TCP代理
|
### 2.4 加密二级TCP代理
|
||||||

|

|
||||||
VPS(IP:22.22.22.33)执行:
|
VPS(IP:22.22.22.33)执行:
|
||||||
`proxy tcp -t tls -p ":33080" -T tcp -P "127.0.0.1:8080" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":33080" -T tcp -P "127.0.0.1:8080" -C proxy.crt -K proxy.key`
|
||||||
本地执行:
|
本地执行:
|
||||||
@ -604,7 +604,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地23080端口就是通过加密TCP隧道访问22.22.22.33的8080端口。
|
那么访问本地23080端口就是通过加密TCP隧道访问22.22.22.33的8080端口。
|
||||||
|
|
||||||
### 2.5 加密三级TCP代理
|
### 2.5 加密三级TCP代理
|
||||||

|

|
||||||
一级TCP代理VPS_01,IP:22.22.22.22
|
一级TCP代理VPS_01,IP:22.22.22.22
|
||||||
`proxy tcp -t tls -p ":38080" -T tcp -P "66.66.66.66:8080" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":38080" -T tcp -P "66.66.66.66:8080" -C proxy.crt -K proxy.key`
|
||||||
二级TCP代理VPS_02,IP:33.33.33.33
|
二级TCP代理VPS_02,IP:33.33.33.33
|
||||||
@ -690,7 +690,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
## 3.UDP代理
|
## 3.UDP代理
|
||||||
|
|
||||||
### 3.1.普通一级UDP代理
|
### 3.1.普通一级UDP代理
|
||||||

|

|
||||||
本地执行:
|
本地执行:
|
||||||
`proxy udp -p ":5353" -T udp -P "8.8.8.8:53"`
|
`proxy udp -p ":5353" -T udp -P "8.8.8.8:53"`
|
||||||
那么访问本地UDP:5353端口就是访问8.8.8.8的UDP:53端口。
|
那么访问本地UDP:5353端口就是访问8.8.8.8的UDP:53端口。
|
||||||
@ -718,7 +718,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
`proxy udp -p ":33080-33085" -T udp -P "192.168.22.33:2222" --lock-port`
|
`proxy udp -p ":33080-33085" -T udp -P "192.168.22.33:2222" --lock-port`
|
||||||
|
|
||||||
### 3.2.普通二级UDP代理
|
### 3.2.普通二级UDP代理
|
||||||

|

|
||||||
VPS(IP:22.22.22.33)执行:
|
VPS(IP:22.22.22.33)执行:
|
||||||
`proxy tcp -p ":33080" -T udp -P "8.8.8.8:53"`
|
`proxy tcp -p ":33080" -T udp -P "8.8.8.8:53"`
|
||||||
本地执行:
|
本地执行:
|
||||||
@ -726,7 +726,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地UDP:5353端口就是通过TCP隧道,通过VPS访问8.8.8.8的UDP:53端口。
|
那么访问本地UDP:5353端口就是通过TCP隧道,通过VPS访问8.8.8.8的UDP:53端口。
|
||||||
|
|
||||||
### 3.3.普通三级UDP代理
|
### 3.3.普通三级UDP代理
|
||||||

|

|
||||||
一级TCP代理VPS_01,IP:22.22.22.22
|
一级TCP代理VPS_01,IP:22.22.22.22
|
||||||
`proxy tcp -p ":38080" -T udp -P "8.8.8.8:53"`
|
`proxy tcp -p ":38080" -T udp -P "8.8.8.8:53"`
|
||||||
二级TCP代理VPS_02,IP:33.33.33.33
|
二级TCP代理VPS_02,IP:33.33.33.33
|
||||||
@ -736,7 +736,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地5353端口就是通过TCP隧道,通过VPS访问8.8.8.8的53端口。
|
那么访问本地5353端口就是通过TCP隧道,通过VPS访问8.8.8.8的53端口。
|
||||||
|
|
||||||
### 3.4.加密二级UDP代理
|
### 3.4.加密二级UDP代理
|
||||||

|

|
||||||
VPS(IP:22.22.22.33)执行:
|
VPS(IP:22.22.22.33)执行:
|
||||||
`proxy tcp -t tls -p ":33080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":33080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
||||||
本地执行:
|
本地执行:
|
||||||
@ -744,7 +744,7 @@ VPS(IP:22.22.22.33)执行:
|
|||||||
那么访问本地UDP:5353端口就是通过加密TCP隧道,通过VPS访问8.8.8.8的UDP:53端口。
|
那么访问本地UDP:5353端口就是通过加密TCP隧道,通过VPS访问8.8.8.8的UDP:53端口。
|
||||||
|
|
||||||
### 3.5.加密三级UDP代理
|
### 3.5.加密三级UDP代理
|
||||||

|

|
||||||
一级TCP代理VPS_01,IP:22.22.22.22
|
一级TCP代理VPS_01,IP:22.22.22.22
|
||||||
`proxy tcp -t tls -p ":38080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
`proxy tcp -t tls -p ":38080" -T udp -P "8.8.8.8:53" -C proxy.crt -K proxy.key`
|
||||||
二级TCP代理VPS_02,IP:33.33.33.33
|
二级TCP代理VPS_02,IP:33.33.33.33
|
||||||
@ -995,14 +995,14 @@ SOCKS5代理,支持CONNECT,UDP协议,不支持BIND,支持用户名密码
|
|||||||
```
|
```
|
||||||
|
|
||||||
### 5.2.普通二级SOCKS5代理
|
### 5.2.普通二级SOCKS5代理
|
||||||

|

|
||||||
使用本地端口8090,假设上级SOCKS5代理是`22.22.22.22:8080`
|
使用本地端口8090,假设上级SOCKS5代理是`22.22.22.22:8080`
|
||||||
`proxy socks -t tcp -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" --udp-port 0 --udp`
|
`proxy socks -t tcp -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" --udp-port 0 --udp`
|
||||||
我们还可以指定网站域名的黑白名单文件,一行一个域名,匹配规则是最右匹配,比如:baidu.com,匹配的是*.*.baidu.com,黑名单的域名域名直接走上级代理,白名单的域名不走上级代理;如果域名即在黑名单又在白名单中,那么黑名单起作用。
|
我们还可以指定网站域名的黑白名单文件,一行一个域名,匹配规则是最右匹配,比如:baidu.com,匹配的是*.*.baidu.com,黑名单的域名域名直接走上级代理,白名单的域名不走上级代理;如果域名即在黑名单又在白名单中,那么黑名单起作用。
|
||||||
`proxy socks -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" -b blocked.txt -d direct.txt --udp-port 0 --udp`
|
`proxy socks -p "0.0.0.0:8090" -T tcp -P "22.22.22.22:8080" -b blocked.txt -d direct.txt --udp-port 0 --udp`
|
||||||
|
|
||||||
### 5.3.SOCKS二级代理(加密)
|
### 5.3.SOCKS二级代理(加密)
|
||||||

|

|
||||||
一级SOCKS代理(VPS,IP:22.22.22.22)
|
一级SOCKS代理(VPS,IP:22.22.22.22)
|
||||||
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
||||||
|
|
||||||
@ -1015,7 +1015,7 @@ SOCKS5代理,支持CONNECT,UDP协议,不支持BIND,支持用户名密码
|
|||||||
然后设置你的windos系统中,需要通过代理上网的程序的代理为socks5模式,地址为:127.0.0.1,端口为:8080,程序即可通过加密通道通过vps上网。
|
然后设置你的windos系统中,需要通过代理上网的程序的代理为socks5模式,地址为:127.0.0.1,端口为:8080,程序即可通过加密通道通过vps上网。
|
||||||
|
|
||||||
### 5.4.SOCKS三级代理(加密)
|
### 5.4.SOCKS三级代理(加密)
|
||||||

|

|
||||||
一级SOCKS代理VPS_01,IP:22.22.22.22
|
一级SOCKS代理VPS_01,IP:22.22.22.22
|
||||||
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
`proxy socks -t tls -p ":38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
||||||
二级SOCKS代理VPS_02,IP:33.33.33.33
|
二级SOCKS代理VPS_02,IP:33.33.33.33
|
||||||
@ -1029,7 +1029,7 @@ SOCKS5代理,支持CONNECT,UDP协议,不支持BIND,支持用户名密码
|
|||||||
`proxy socks --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
`proxy socks --always -t tls -p ":28080" -T tls -P "22.22.22.22:38080" -C proxy.crt -K proxy.key --udp-port 0 --udp`
|
||||||
|
|
||||||
### 5.6.SOCKS通过SSH中转
|
### 5.6.SOCKS通过SSH中转
|
||||||

|

|
||||||
说明:ssh中转的原理是利用了ssh的转发功能,就是你连接上ssh之后,可以通过ssh代理访问目标地址。
|
说明:ssh中转的原理是利用了ssh的转发功能,就是你连接上ssh之后,可以通过ssh代理访问目标地址。
|
||||||
假设有:vps
|
假设有:vps
|
||||||
- IP是2.2.2.2, ssh端口是22, ssh用户名是:user, ssh用户密码是:demo
|
- IP是2.2.2.2, ssh端口是22, ssh用户名是:user, ssh用户密码是:demo
|
||||||
@ -1277,7 +1277,7 @@ SPS上级和本地支持ss协议,上级可以是SPS或者标准的ss服务,
|
|||||||
`proxy sps -S ss -H aes-256-cfb -J pass -T tcp -P 127.0.0.1:8080 -t tcp -p :18080 -h aes-192-cfb -j pass`。
|
`proxy sps -S ss -H aes-256-cfb -J pass -T tcp -P 127.0.0.1:8080 -t tcp -p :18080 -h aes-192-cfb -j pass`。
|
||||||
|
|
||||||
### 6.5 链式连接
|
### 6.5 链式连接
|
||||||

|

|
||||||
上面提过多个sps结点可以层级连接构建加密通道,假设有如下vps和家里的pc电脑。
|
上面提过多个sps结点可以层级连接构建加密通道,假设有如下vps和家里的pc电脑。
|
||||||
vps01:2.2.2.2
|
vps01:2.2.2.2
|
||||||
vps02:3.3.3.3
|
vps02:3.3.3.3
|
||||||
@ -1826,7 +1826,7 @@ bytes: 此次使用的流量字节数.
|
|||||||
|
|
||||||
#### 流量上报原理
|
#### 流量上报原理
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
### 主动断开用户连接
|
### 主动断开用户连接
|
||||||
|
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user